ECIT
شركة متخصصة في البرمجيات الحديثة
تطوير الأنظمة
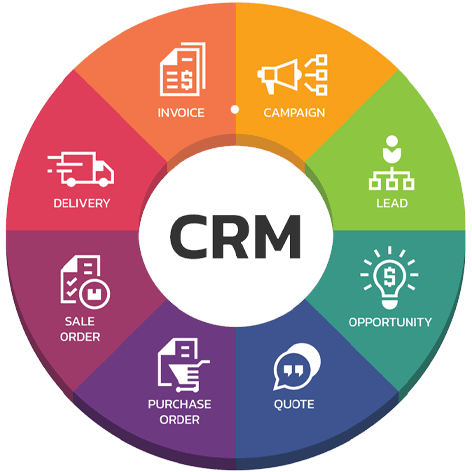
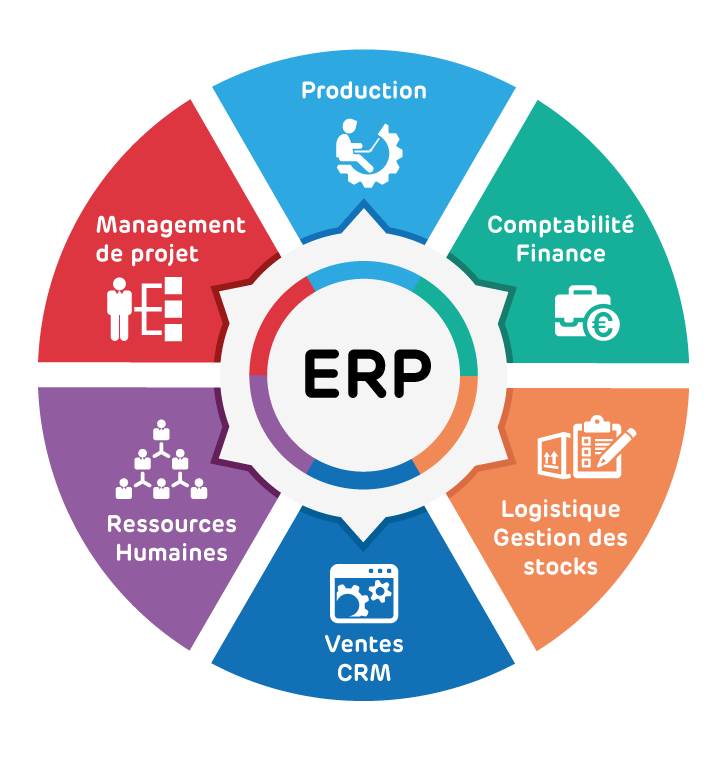
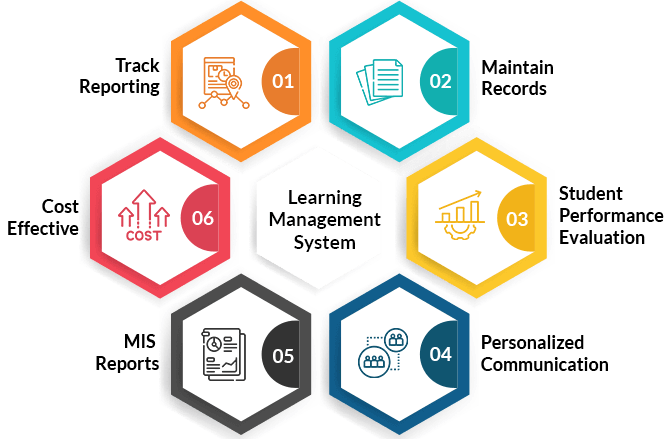
نحن نقدم أنواعًا مختلفة من أنظمة إدارة البرامج مثل أنظمة ERP و CMS و LMs.
بناء التطبيقات
نبني تطبيقات جوال قوية ومتطورة، تجمع بين التصميم الجذاب والأداء العالي، مما يضمن تجربة مستخدم استثنائية ويجذب انتباه جمهورك المستهدف .
تطوير صفحات الويب
نحن نطور مواقع إلكترونية تهدف إلى تسهيل التواصل الفعّال مع جمهورك وتعزيز العلاقات القوية. فنحن نفهم أن التواصل المستمر مع الجمهور هو مفتاح النجاح في العالم الرقمي.
من نحن !
شركة متخصصة في البرمجيات الحديثة
شركة خبراء تقنية المعلومات حريصون على أن نحقق التزامنا الدائم بالتوافق مع رؤية المملكة العربية السعودية 2030 من خلال تقديم وتسليم مشاريع عالية الكفاءة والجودة، وتوفير الدعم لفرق العمل المُتحفِّزة والمرنة، ذات التركيز الكبير. علاوة على أننا نُقدِّر أهمية علاقاتنا، وملتزمون في التعامل بنزاهة وموضوعية مع جميع العملاء والمُورِّدين والشركاء. باختصار، نحن نساعد المنظمات العصرية على جعل خدماتها لتقنية المعلومات تستجيب لمتطلبات قطاع أعمالها.
التقنيات المستخدمة في شركتنا






مشروعك تحت إشراف مطورين وخبراء تقنيين
ECIT
شركة خبراء تقنية المعلومات ECIT تمتلك الخبراء للعمل على دراسة المشاريع والإشراف على تنفيذها بكل معايير الدقة والجودة.
ECIT
رحلة العميل معنا
 1
1
تخطيط
 2
2
جمع المتطلبات
 3
3
البرمجة والتجربة
 4
4
النتيجة النهائية






